LAW ENFORCEMENT technology and IT forensics
Details- Investigative analysis systems
- Standardization and analysis of financial data
- Analysis of retained data in GSM communication
- OSINT (Open Source Intelligence) solutions
- COM-INT Monitoring
- Detection and protection against drones
Investigative analysis systems
Details
Matic SA delivers and implements i2, a comprehensive intelligence analysis system . i2 is a family of products which combine their rich analytical potential and visualization features with real-time information sharing capabilities.
The solution helps analysts and intelligence teams at all stages of investigation. i2 products are flexible, secure, easy to implement and user-friendly. They are used both in simple and in complex environments for identification, prediction and prevention of organized crime, corruption, terrorists and economic crime, such as fraud.
i2 intelligence analysis tools provide effective visualization, analysis and advanced data access features. This means spending less time on data processing and increases the time available for its analysis. The flexible data model and the visualization environment, combined with a rich visual analytical toolset, aids the user in building a variety of analytical views of the same data. More emphasis can be applied to the structure of relationships, or one can focus on the chronology of events.
i2 intelligence analysis solutions have become a standard in the development of intelligence and investigative analytics worldwide. The platform’s flagship product, Analyst’s Notebook, is currently in use in more than 150 countries and has been localized to 18 languages (including Polish). i2 offers extremely flexible tools designed to map and transform information imported from structural or non-structural data sources and stored in a centralized repository. Once the information has been modeled into a unified format, users can reach for data management tools to identify duplicate data and discover convergence with data sources which had so far been considered unrelated.
If your organization has a need to analyze heterogeneous data, present results of your operations, organize information or benefit from easy access to the existing data sources, i2 shall be your correct choice.
Standardization and analysis of financial data
Details
Matic SA’s mAnalyzer solution is intended for the standardization and analysis of financial data and to make it available in the form of structured external analytical tools.
The system is equipped with an import engine that provides processing and collection of bank statements in various formats such as TXT / CSV / XLSX / PDF and others.
The imported data is stored in the built-in PostgreSQL database.
The system has built-in mechanisms for controlling data import. Import results are saved in the database in the form of import history.
Identity
The system distinguishes the following types of identities:
- Company
- Person
- Credit card
You can assign one or many bank accounts to each identity. While working with the application, it is possible to merge both bank accounts and entire identities.
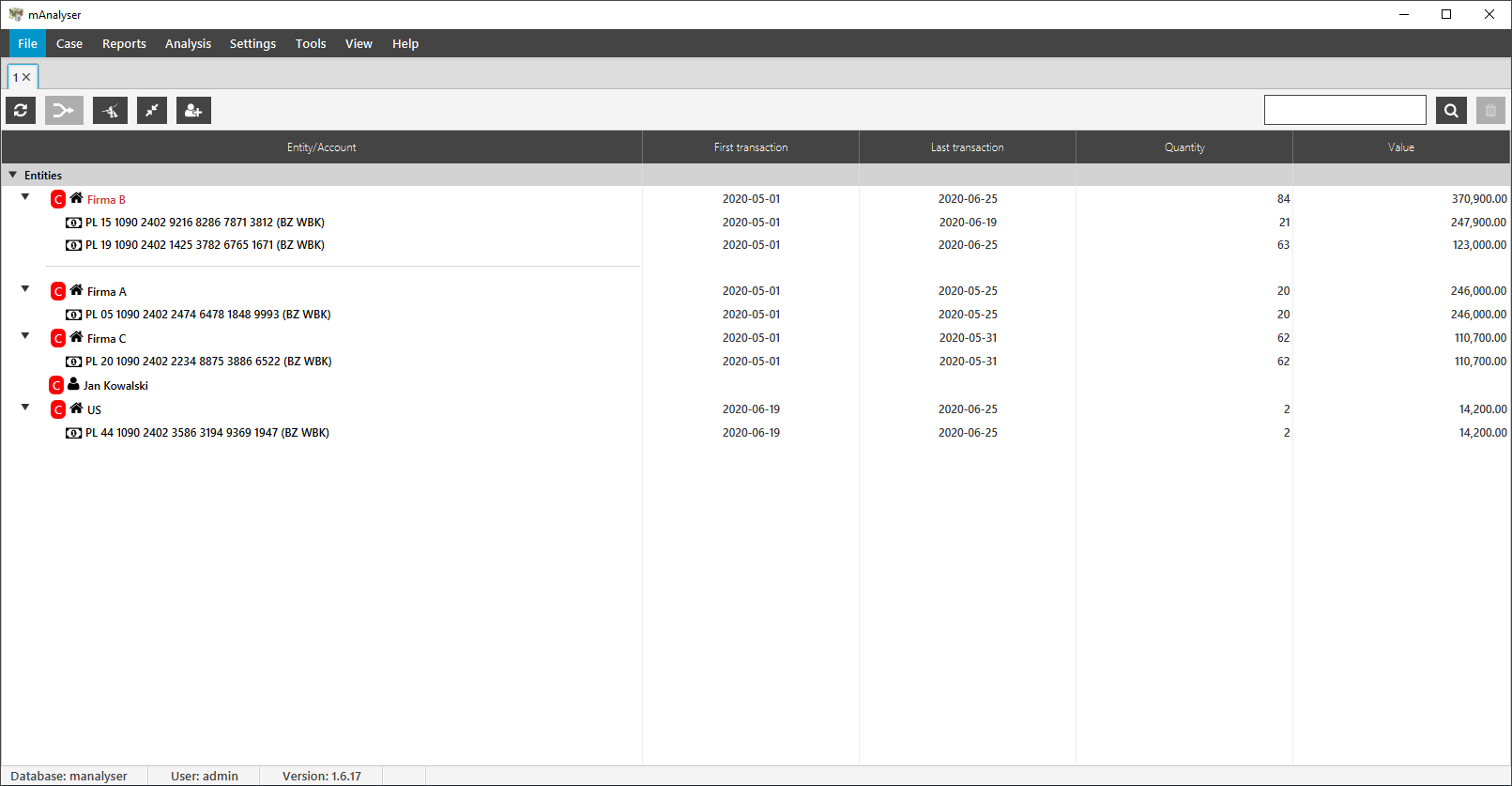
Data presentation and analysis
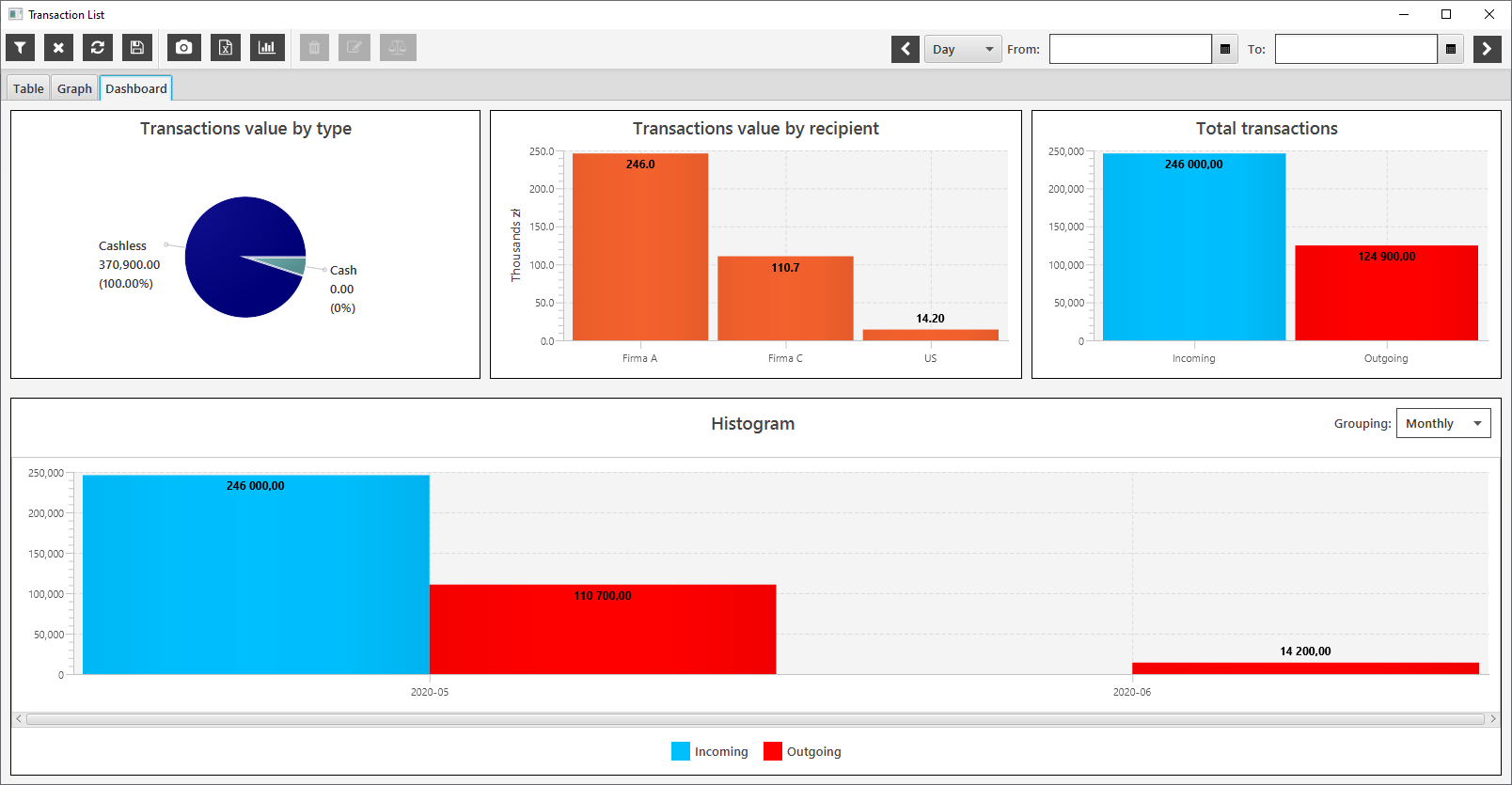
The imported data can be filtered and presented in tabular form, or on dashboards.
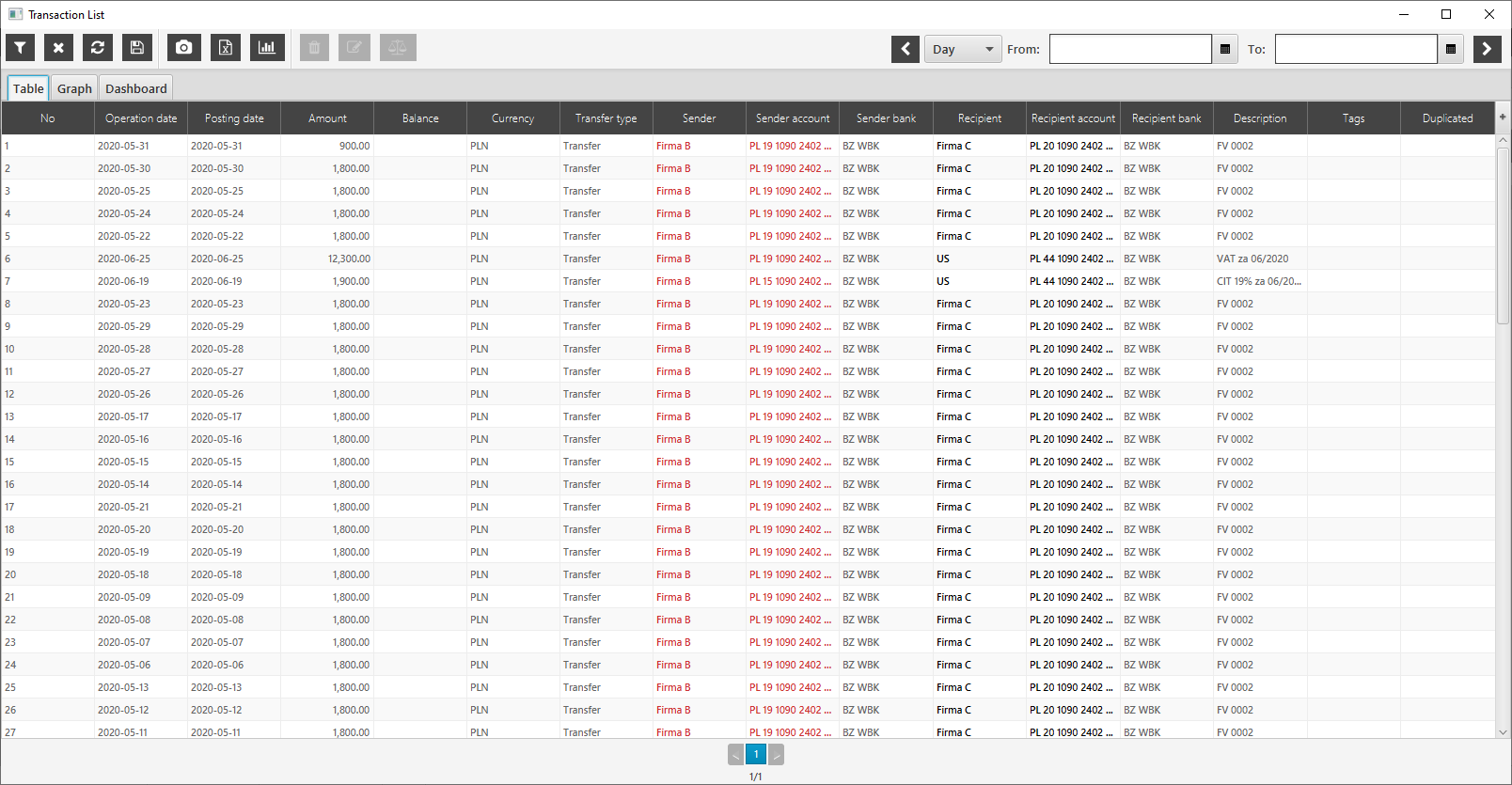
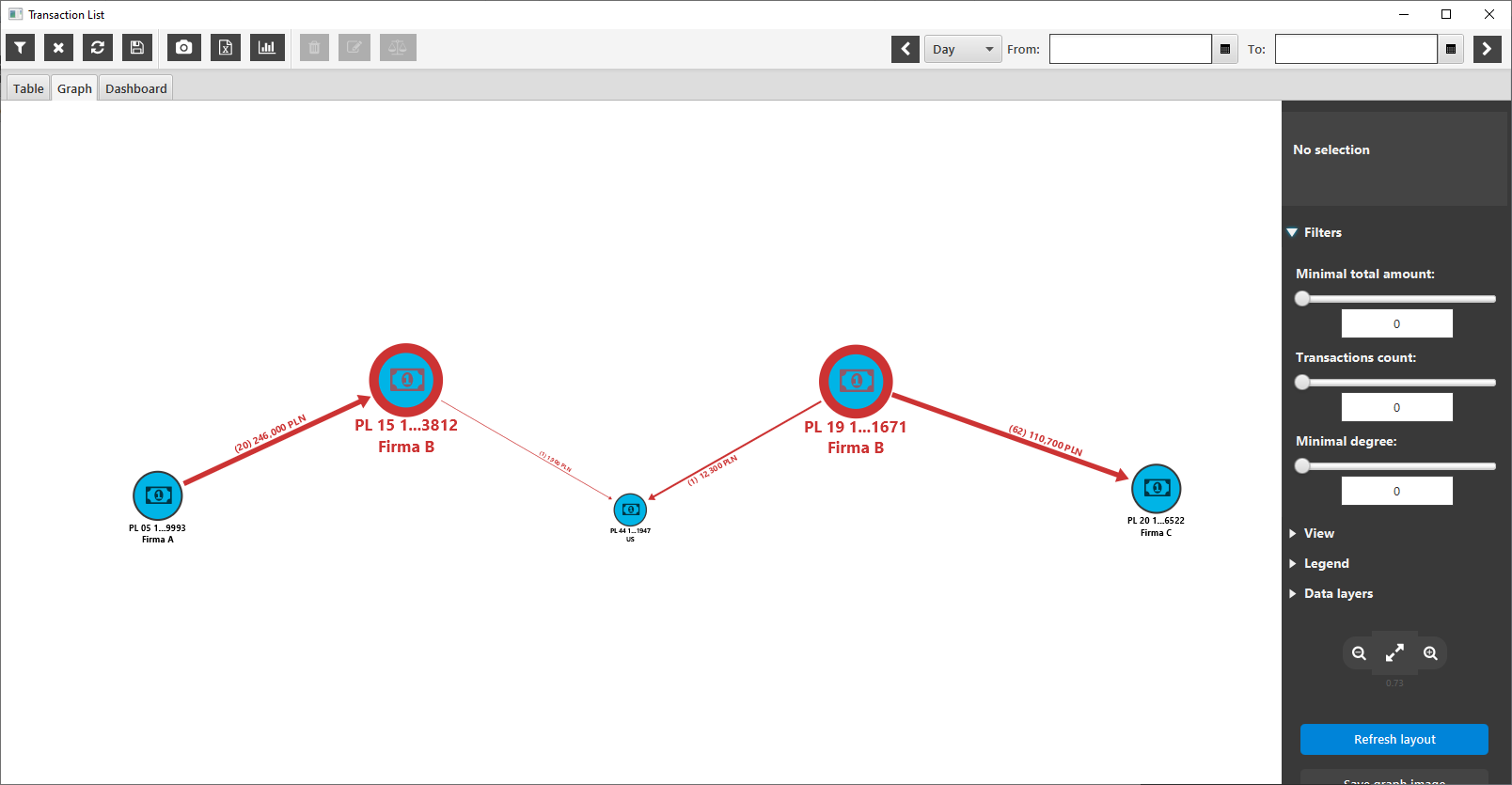
Integration with IBM i2 software
The system is integrated with IBM i2 software and allows you to visualize data on IBM i2 Analyst’s Notebook diagrams, as well as export financial data to other IBM i2 tools, such as IBM i2 iBase, or IBM i2 Enterprise Insight Analysis.
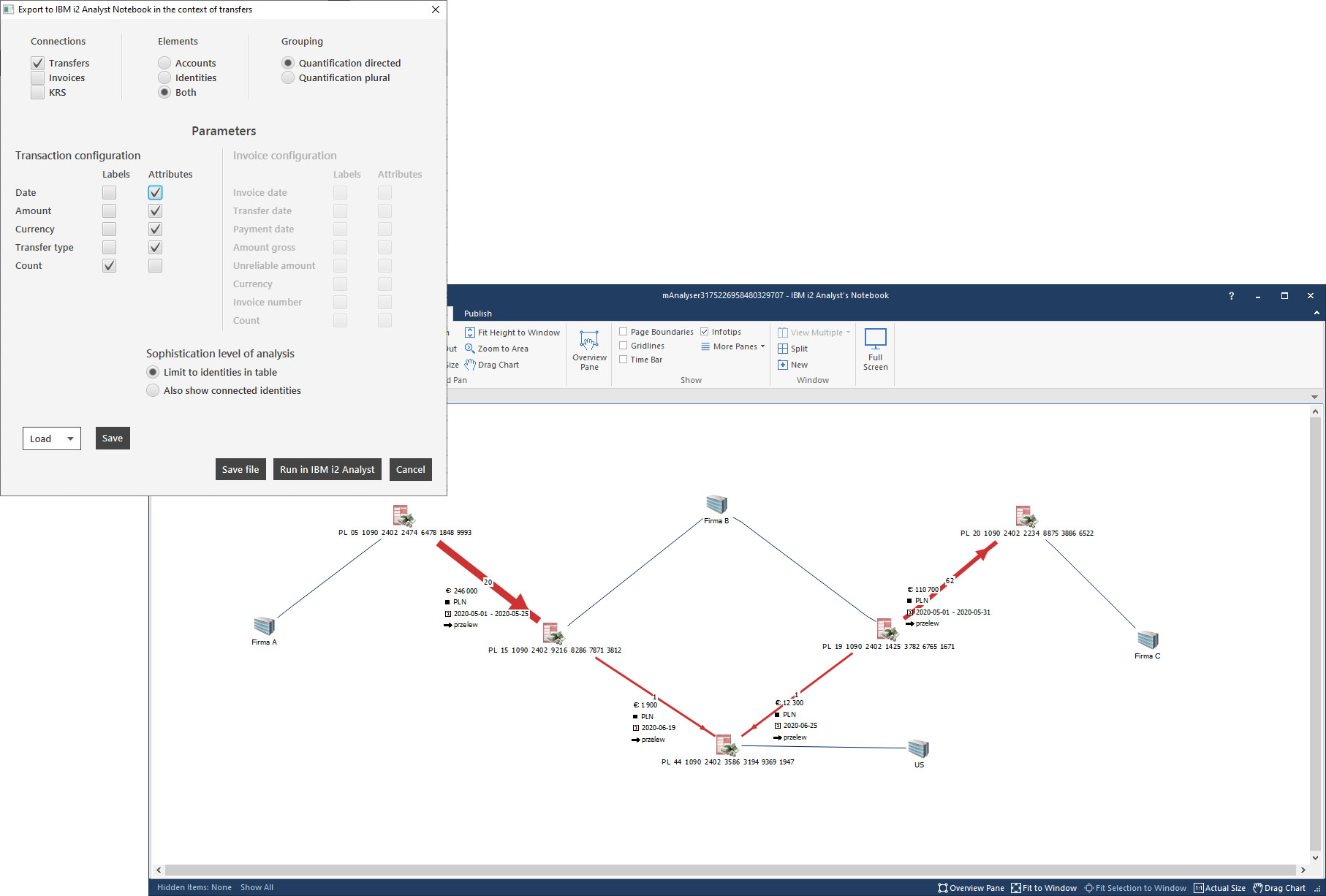
Reports
The system has defined templates for generating reports.
Analysis of retained data in GSM communication
Details
Matic SA offers Mercure, a versatile solution from Ockham Solutions, designed by the French development company as a dedicated suite for detailed analysis of call detail records (CDRs), base transceiver station data (BTS logs), call logs and mobile phone memory and SIM card data. All those capabilities make Mercure the best-in-class tool for investigators and analysts of specialized units and law enforcement organizations.
Mercure can automatically recognize more than 500 data formats used by telecom companies in numerous countries, including without limitation mobile operators active in Poland, France, Belgium, Spain, UK, Netherlands, South Africa, Australia or Morocco. The software offers an efficient toolset for all types of investigations, regardless of their sizes and complexity, which makes it suitable for cases that involve analyzing millions of calls.
With more than 40 built-in queries dedicated to call data research, it enables executing even the most advanced forensic tasks in a click or two. The key features of the product include:
- A large correlation table between detailed billing, base station and export from phone and SIM cards
- Search for key people (linkers of environments)
- Search for subscribers’ habits
- Assigning attributes to telephone sets
- Identifying the way criminal groups operate at the crime scene
- Route detection and geolocation (OpenStreetMap)
- Identification of shared IMSI / IMEI between suspects
- Detection of connections between SIM cards and telephone sets
- Study of synchronized behaviors within a group of people
- Typing of likely meeting places on the map
- Automatic export of the analysis result to IBM i2 Analyst’s Notebook
- Analysis of chats from mobile applications, including Facebook, Skype, Viber, WhatsApp, Kik, Twitter
OSINT (Open Source Intelligence) solutions
Details
The information that is publicly available online is a valuable source of intelligence for forensic investigators, as criminal groups and terrorists use the Internet to communicate with each other and organize their activities.
Matic SA provides solutions designed to facilitate obtaining intelligence from such sources and running investigations online in response to the key challenges of the modern world:
Law enforcement
- Organized crime and gangs
- Pedophilia
- Identity theft and extortion
- Money laundering
- Crimes in the area of intellectual property infringement
- Identification and development of extremist organizations
Online recruitment and influencing
- Identification of key individuals and activists
- Real-time monitoring of opponents’ networks
- Organic dissemination of information
- Influencing public opinion
National security and defense
- Identification and researching of terrorist organizations
- Risks for public transport
- Sanctions and legal requirements
- Analysis of opponents’ knowledge bases (HME, IED, TTPs)
- Geolocation of targets
- Support for military operations
Online crime and hacker activity
- Supporting protection of ICT networks by finding out:
- Who is attacking your organization?
- What are their motives?
- How are they organised?
- What are their tools?
Matic SA supplies the solutions that enable you to:
- Analyze relationships and gather information from social networks, such as Facebook, Twitter or VK
- Search the Internet for specific content and events
- Aggregate the information obtained from the Internet as intelligence gathered as part of a specific investigation
- Manage online investigations
- Gather and identify evidence, evaluate its credibility
- Manage identities
- Monitor online activist identities and groups
- Work with the information obtained on the dark web
- Identify individuals and locations, e.g. using geolocation tools
COM-INT Monitoring
Details
Support for the full data acquisition for electronic reconnaissance and intelligence activities.
Ground-breaking changes in the modern communications
Communication means exchange of information. The volume and the structure of communication have undergone unprecedented changes in the recent years, revolutionizing it. Information exchange has turned electronic in a most unpredictably abrupt and surprising way. Even voice communication is becoming digital in its format. Telecoms have built structurally unified data and voice transmission networks, and social networks and instant messaging have become significant communication channels.
New challenges in acquisition of reliable intelligence data
The traditional means of communications, such as phone landlines, mobile or satellite phones and military radio communications are nowadays increasingly often replaced by IP-based solutions. One of the consequences of this ongoing change is the vast diversity of the communication protocols that need to be correctly parsed if the valuable information they are used to transmit is to be captured. Investigating groups of sources or complex networks unavoidably brings even more challenges about.
Target monitoring calls for new tools
Once targets have been found and identified, their effective monitoring is impossible without the ability to access and analyse multiple sources of information at the same time. For example, limiting surveillance to mobile telephony communications may result in overlooking some parts of communication of critical importance to the understanding of the target’s actions and intents. In order to avoid this, new means, methods and techniques need to be implemented, such as a broad variety of sensors, correlation of events from diverse sources, powerful communications content analysis tools and extremely complex data analysis and filtering capabilities.
Finding a needle in the data haystack
While following and monitoring the targets which have already been identified is a challenging task, identifying new targets or potential threats entails going one step further, as it often requires extracting raw data from selected sensors. This, in turn, frequently means a need to process vast amounts of data that has to be interpreted with smart filters and sophisticated models that enable finding the desired bits of information. It may also require the use of data streaming mechanisms that allow linear scaling regardless of the information volume.
Detection and protection against drones
Details
Incidents of unauthorized drone activity in the area belonging to airports, enclosed areas, prisons or attempts to transfer dangerous goods by them: weapons, chemical or biological agents as well as fissile materials are being reported more and more frequently.
Drones can also be used for terrorist attacks and pose a threat to mass events.
In response to threats Matic SA offers drone detection and protection systems manufactured by MyDefence.
The motto of MyDefence is the idea of “protecting those who protect us” and its offer is directed mainly to the armed forces, police, special services, prison services and border protection services.
WINGMAN
A handheld, personal detector capable of detecting remotely controlled commercial drones (UAV, AUS, RPAS) from a considerable distance – and often before launch.
WINGMAN is worn on the torso or on the outer part of the clothes and is equipped with an internal lithium battery ensuring full autonomy. It works both as an independent unit and as a peripheral device connected to other devices, such as a personal communication radio. Thanks to the external radio, it is possible to integrate your drone detection system with any existing communication and positioning system.
WINGMAN constantly scans and searches for UAV control channels, and the continuous scan function allows you to detect a repeating frequency or a drone control signal. The device emits audible, vibrating or pulsing alarms using the LED diode.
The unique performance of the WINGMAN, a light yet robust and waterproof housing, makes it one of the smallest and most effective drone detectors available on the market today. It is intended for officers of security forces, special forces and personal security agents.
WATCHDOG
A radio frequency sensor that allows the user to identify the brand and the drone model by searching for signals to control it.
WATCHDOG can be used in a mobile or stationary version, in which it is an ideal solution for perimeter protection of a large area or protection of facilities and installations.
In particular, it is suitable for protection of military bases, airports, government buildings, embassies and penitentiary centers.
The device is very easy to use. They can be installed on a tree or pole using fixing points and set up in a few minutes.
Thanks to one cable system, WATCHDOG can be used for fast protection of distant military bases, training areas, airports, penitentiary centers, centers for refugees and borders of the state.
Due to the small size WATCHDOG can easily integrate into the existing spatial infrastructure. The configuration of the network cable allows you to install the WATCHDOG device as perimeter protection along, for example, fences or walls, to protect against drones performing reconnaissance functions.
In the network configuration, WATCHDOG allows you to get information about the detected drones. Thanks to this, you can act quickly and precisely to respond to existing threats.
Application of the detection and protection system against drones
- Securing VIPs and convoys
- Protection of critical infrastructure facilities, military facilities and installations
- Counteracting espionage, recognition and cyber attacks from the air
- Protection of government buildings, embassies
- Ensuring safety during public gatherings, sporting events and concerts
System functionalities
- Real-time detection and alarm
- Active counteraction and protection
- Records of monitoring and incident reporting
- Central register of events