Cybersecurity
Details- Training and education
- Vulnerability management systems
- SIEM solutions
- Data security on mobile devices
- Internal network security systems
Training and education
Details
Having competence in the field of cyber security is an important element of security. Lack of protection in the field of cyber security threatens to maintain a normally functioning country in the social layer, public information (media), ensure effective communication in the processes of supply and production or maintain key systems for industrial safety in waterworks, refineries, pipelines, fuel bases, energy networks and many other objects that have a direct impact on human life and health.
At Matic SA, we have a wide portfolio of solutions aimed at ensuring the security of digital resources, telecommunications networks and critical infrastructure. This area is one of the key elements of the company’s operations.
Together with our Partner – PGI, we offer a comprehensive training program in the field of cyber security. The courses cover the following topics:
- Cybersecurity management – a set of dedicated courses for management and senior level commanders
- Advanced methods of conducting cyber attacks – courses designed for technical specialists to conduct operations
- Collecting digital evidence (investigation analysis) – a course directed mainly for police and prosecutors in the area of securing and searching for process evidence in the digital space
- Analytical skills in cybersecurity – course for strategic analysts
- Open source intelligence – intelligence gathering in public space
- Government programs – dedicated courses for government agencies, the army and special services
- Data and protocols in telecommunications networks – trainings allowing to understand the meaning of technical information sent in telecommunications networks.
The PGI Cybersecurity Academy offers the highest level of training for business and government organizations, being a comprehensive center that combats threats in the field of digital protection and cybersecurity for all industrial sectors.
The courses have been specifically designed for:
- Commanding personnel who must ensure the security of their organizations – also in the field of defending reputation, brand and media control in propaganda attacks
- Government agencies responsible for ensuring public order and defense in the area of cyberspace
- IT leaders who want to create business value and IT strategy with attention to the defense of the network and critical data
- IT professionals in industries where it is necessary to be able to protect systems in real time
- International organizations
We decided to cooperate with the cyber security academy PGI, because:
- Cybersecurity Academy PGI offers a unique approach in terms of design, technology and use of the training environment (Cyber simulator)
- Coaches are carefully selected, with operational experience in government agencies. They are the highest world class experts in their fields, who combine training and learning with the implementation of operational tasks – maintaining a constantly current level of knowledge
- All courses are convergent with defense objectives, in particular by NATO standards or accreditations such as CESG, CREST and TIGER
- All trainings are tailored to the industry characteristics and tasks
- All participants of PGI trainings become part of the Alumni program, which allows for further exchange of professional experience and contacts
Vulnerability management systems
Details
We offer IT systems vulnerability/weakness detection services (vulnerability tests) based on QualysGuard technology.
The service is available in annual subscription for a defined number of IP addresses or specific Web applications. We also offer single vulnerability scans with scanning option selection.
QualysGuard is a service which does not require any hardware or software purchases.
It substantially simplifies and automates vulnerability management in complex corporate network environments. QualysGuard keeps listing the networked resources (so that it is impossible to hide a “foreign” device with a separate IP address), detecting non-protected ports and runs an automated search for vulnerabilities in the organisation’s IT resources. At the same time, the service is checking compliance with the internal security policies and external regulations (including ISO 27001).
All vulnerabilities discovered are described and linked to the existing threats. Each such discovery is accompanied with recommended countermeasures which should be used to eliminate it. The scanning engines are capable of detecting vulnerabilities on server machines, workstations, in operating systems, applications, databases and any other appliances that have their own IP address. In order to specify the scanning range, the customer needs to input IP addresses or names of the web applications to be included in the scan. The scanner can test all kinds of devices connected to the computer network that communicate over TCP-IP.
QualysGuard (QG) is composed of five modules which form an integrated environment available online on the service’s dashboard:
- VM (Vulnerability Management) module: detection of vulnerabilities, their descriptions including the details of existing correlated malicious software, description of countermeasures, risk management information and an indication of the availability of an option to generate a delta report, a test that compares scanning results before and after repair
- PC (Policy Compliance) module, which validates the ICT resources security test results against the adopted security policy
- PCI (PCI compliance) module, which validates the ICT resources security test results against the PCI DSS standard (for ICT systems which support card-based payments)
- WAS (Web Application Scanning) module, which checks the security of web applications
- MD (Malware Detection) module, which detects malware on website pages
SIEM solutions
Details
Matic delivers and implements QRadar, a SIEM solution from IBM.
QRadar consolidates and combines security incident data from thousands of Client’s distributed devices and applications. Next, it instantly correlates the raw data to distinguish the real threats from false alarms. The software can optionally be integrated with IBM’s Security X-Force Threat Intelligence online platform, which provides lists of IP addresses that are potential sources of attacks, such as hosts running malware, spam mailers and other threats. IBM Security QRadar SIEM can also link security vulnerabilities to incident data and the organisation’s network activity to help determine the priorities for the security incident response team.
IBM Security QRadar SIEM:
- Provides near-real-time updates of the current security status, helping in threat detection and prioritisation, and thus facilitating monitoring of the entire IT infrastructure
- Limits the number of alerts and assigns priorities to them, effectively short-listing the security incidents that require investigation
- Helps increase the efficiency of threat detection and enables responding to them effectively, while also serving as a source of detailed reports on user access and activity
- Provides smart protection to cloud environments
- Generates detailed reports on user’s access to data and user activity, helping achieve compliance.
Data security on mobile devices
Details
Our portfolio includes a system for professional management of mobile devices, such as PDAs, smartphones and laptops.
The system is based on IBM MobileFirst, a product which aids front office field staff by securing confidential and restricted data outside the secure walls of the central office. We guarantee the application of controls and security measures of mobile resources over their entire life.
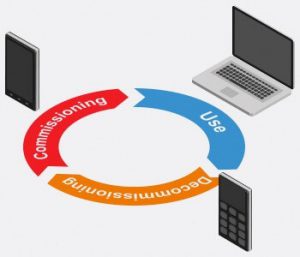
Mobile device life cycle
Mobile environments are heterogeneous, complex and often tend to slip out of control of the head office IT team. The IBM solution gives the IT organization the ability to centralize device and data management and aids their maintenance over their entire life cycle. Each device has a life cycle composed of three stages, each of which is associated with its own set of significant issues, which all need to be dealt with by the companies’ IT departments. In addition, each of those stages requires proactive management of data, devices, applications and communication with all mobile employees. The organizations which use a centralized approach to data and device management provide their information technology staff with appropriate means of control and monitoring, while on the other hand they enable their mobile employees to use the information and the applications they need in their work securely.
Commissioning
At the first stage of the life cycle, IBM solution can be used to manage the tasks of all kinds of mobile initiatives, such as allocation to groups or policy-making, setting up devices to ensure their mutual connectivity, wireless distribution of the management client software or the initial implementation of applications. As far as security is concerned at that stage, IBM enables IT departments to centralize managing security requirements, including establishing security rules, initialization of the passwords entered upon device start-up, installing and encrypting data, installing antivirus software and firewalls, and controlling the ports and I/O systems on each specific device.
Use
At the stage of device use, IBM offers features that help manage routine tasks required to ensure effective and optimised device performance and to automate it. Such tasks include resource tracking, updates and patches, monitoring of device operation, remote controlling, maintaining and modifying the setup of devices and applications and distribution and updates of data and files. IBM MobileFirst can automate electronic file distribution, managing files and directories, notifications and system registry management tasks. The key security tasks include regular data backups, installation of patches and security updates, enforcement of security rules and monitoring the device for security breaches and threats. Administrators can protect the data stored on devices using the latest generation encryption secured with a password which needs to be input upon device start-up (with anti-tamper control) and enforce data access restrictions based on the defined user privileges.
Decommissioning
A mobile device can enter that third stage of its life cycle under a variety of circumstances. The device can be lost, stolen, withdrawn from use or assigned to other purposes. If it has been lost or stolen, IBM MobileFirst’s administration panel allows deleting of data permanently from the device and blocking it. If needed, the administrators can use the system’s tools to re-commission the piece of equipment, deploy software to it or restore its data.
Internal network security systems
Details
The networks of today are known for their dynamics. Threats never stop evolving and become more and more sophisticated. Network security gaps keep emerging because the static protection (firewall, antivirus) is unable to secure dynamic networks against dynamic threats.
Real-time internal network security.
Protection of the internal network calls for a robust IPS (Intrusion Prevention System).
Real-time network traffic is continuously analyzed (event review system) and any unusual behaviors found in the network (repeated login attempts, scanning tests and many more) are blocked, while instant threat alerts are sent to administrators.
Sourcefire IPS uses powerful combinations of methods based on security gap and irregularity detection – with line throughput up to 10 Gbps – to analyze traffic and prevent threats which can damage your network . Whether implemented in the perimeter part of the network, in its demilitarized zone (DMZ), its core or critical parts, the easy-to-use IPS appliances will provide you with end-to-end protection against potential threats.
Virtual environment security
Virtualisation is attracting a lot of threats. They include VM expansion (their growth without proper coordination or control), missing division of duties, no insight in the virtual network communication and gaps in hypervisor protection.
Virtual hosts are very much like their physical counterparts – they must be secured, too:
3D Sourcefire are virtual sensors which launch Sourcefire IPS™ (an intrusion prevention system) can detect attacks against virtual machines as well as ones originating in them.
Sourcefire RNA® (Real-time Network Awareness), which is a real-time network monitoring technology implemented in virtual 3D sensors, can collect VM attributes while assuming the machines belong to the same network segment as the virtual 3D sensor. In order to be effective in preventing VM expansion, RNA recognises the vendors of network interfaces (NICs), both the physical and the virtual ones, which allows clients to identify new hosts as physical or virtual machines. If the new host is a virtual machine, IT security can be alerted to check its compliance.